Take Control of Your Documents with Pydio Cells Advanced Admin
Since day one, Pydio has been designed for teams, providing data organization and access that other open-source solutions simply can’t compete with. Even in the days of Ajaxplorer (Pydio’s predecessor), the software included the concept of Workspaces giving access to a restricted subset of documents. And role-based access control (RBAC) has been present since the beginning; it’s the basis of permission granularity, which allows companies to restrict access to a given group of users to minimize the risk to sensitive data.
Our experience working with large organizations with serious security needs, plus the rewrite of Pydio in GO in 2019, pushed Cell’s data governance capabilities to a new level. Decoupling data sources (actual storage mount points) from workspaces enabled Pydio to introduce a range of Access Control management tools and Audit reports. These tools maximize flexibility and security and give admins the tools they need to stay in control of their organization’s documents.
Let’s look at a few key admin features:
A - Role-based + Rule-based Inheritance
Decoupling Storage (Datasources) from Users' Virtualized Views
Thanks to micro-services, documents are transparently mounted from different servers or object storage. They’re all indexed and gathered into a unique data hierarchy managed by the data administrator. To provide access to a folder from the global tree, an admin creates a Workspace (basically an Access Control flag in the tree), then grants read and/or write permissions to a list of roles (see below).
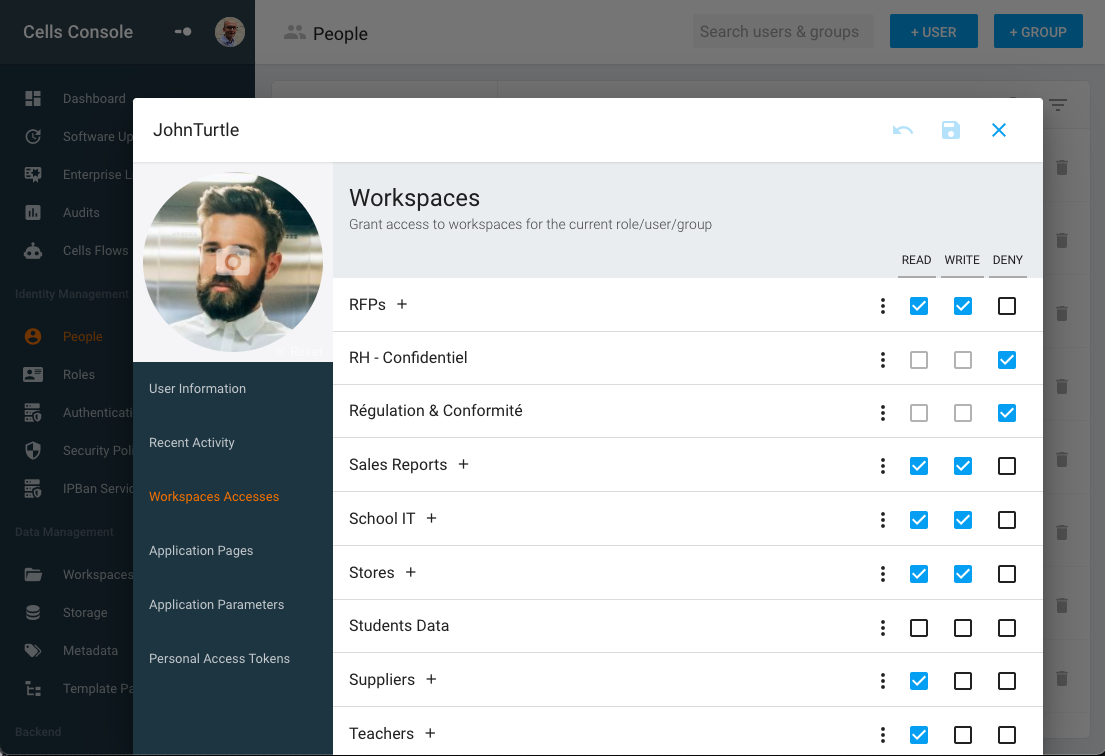
From the user’s point of view, Workspaces appear as the top-level folders they access to find their docs. They’re listed in the left-hand column, and the default layout provides a My Files workspace (pointing to a personal username folder) and a Common Files workspace (shared across users). But in most organizations, administrators create workspaces per department, business unit, or even per project – using whichever paradigm best fits the way their organization breaks down its work.
RBAC Applied to User, Groups and Roles
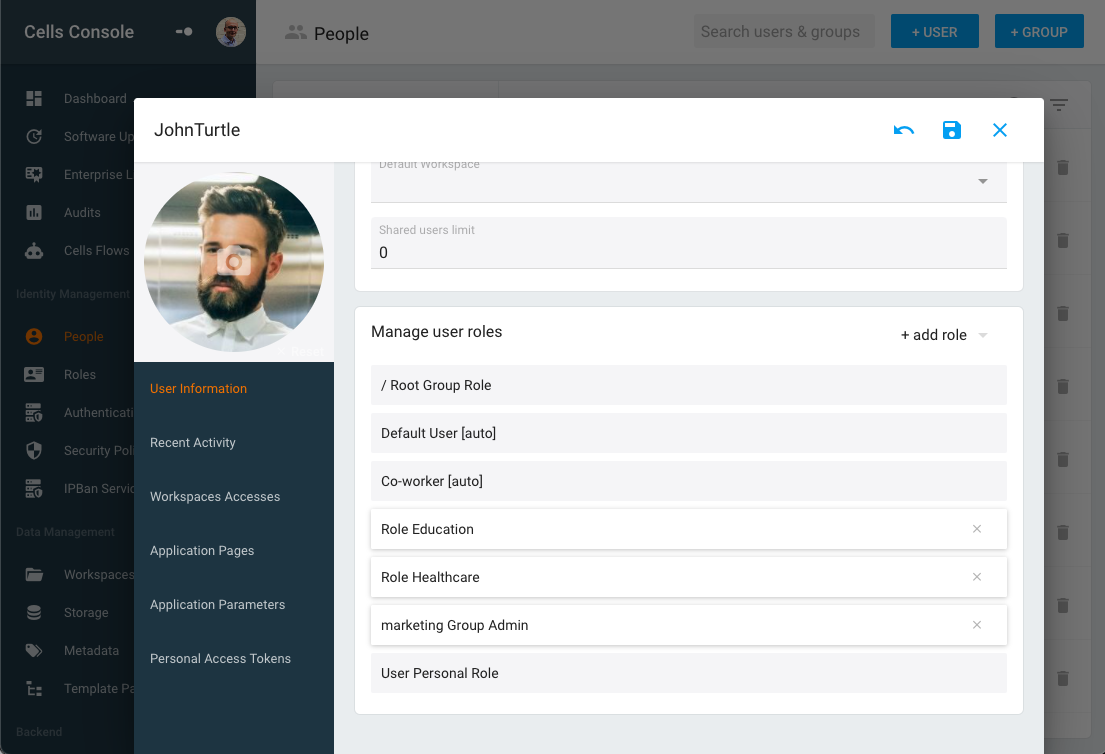
User directories can be imported from internal directories (like AD / LDAP or SSO providers like OIDC/SAML) and managed and stored in the Cells internal database. Directories are organized into Groups (hierarchical organization, one user belongs to one group), where every user has a Profile (roles: standard, shared or admin). You can manually assign one or many roles. Each group is associated with a specific role. Users are also associated with a specific role.
As a result, users can simply be seen as the addition of all the roles they inherit depending on their position in the groups’ hierarchy and the roles manually assigned by the admin. As you’ll remember from the previous section, access control lists are attached to roles:
- Root Role
- Parent Groups Roles
- Manually assigned Role
- User Role
These roles (and their ACLs) are combined with the following rules:
- Deny by default: no access is opened until an ACL is not found in any role
- Combined in descending order: from « Root Role » to « User Role »
- Last one wins: if an ACL is found, it will override the previous value
- Explicit deny breaks inheritance: an ACL can open a Read or Write access but can also explicitly deny access to a resource. Any other permission is ignored and overridden.
This approach provides great flexibility! Let’s look at an example:
- Root Role has Read/Write permission on “My Files,” ReadOnly on “Common Files”
- Admin Role has Read/Write permissions on “Common Files”
- Each Group “GroupName” has a Read/Write on “GroupName Files”
As a result:
- All standard users have R/W on their own workspace (My Files), their group workspace (GroupName Files) and Read-only on Common Files.
- Only Administrators have R/W permissions on Common Files.
B - Rule-Based Security Policies for Dynamic Access
Cells Enterprise provides an additional layer of flexibility with Security Policies. These “rule-based” policies can determine “read/write” permissions by evaluating user-defined rules dynamically, taking into account the context (who is connected, when and from where).
This approach was inspired by Amazon’s IAM Rules, and each policy combines a set of rules based on request metadata:
- Server Time
- Client request origin: CIDR network condition
- Access hostname: used to connect (using Cells multi-site configurations)
- Request method: GET, POST, PUT, etc. and Headers (User-Agent, Cookies, etc.)
- Node metadata: when a request provides a path to a folder or a file (e.g. downloading a file), check this node metadata (file or folder type, file extension, user-defined metadata value, etc.)
- and more...
All this metadata can be “compared” to a reference value with various operations (matches, contains, before/after, etc..).
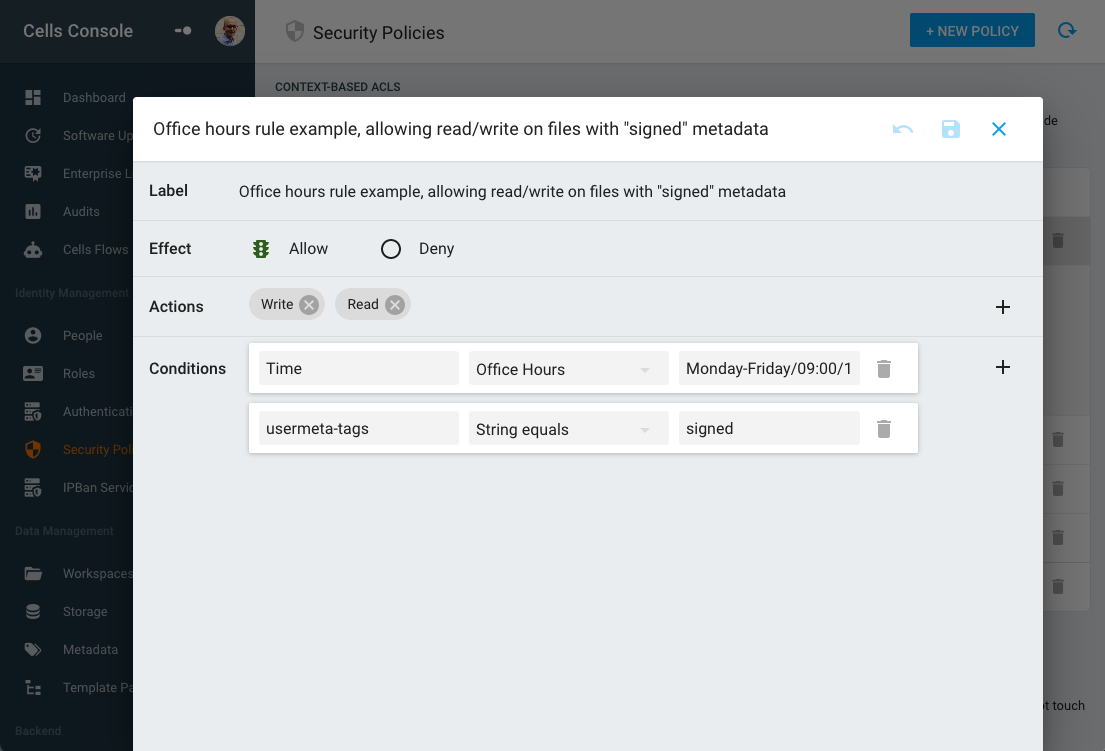
For example, a policy can be defined to forbid connection when not during office hours time or when not inside the local network, or prevent creation/display of specific files based on their extension, or disable download of files based on a user-defined tag (e.g. “confidential”), etc.
C - User Empowerment with Cells
While the administrator defines all these “role-based” and “rule-based” access controls, we don’t want users to have to call support just to share a folder—this is where Cells come into play. Cells are sandboxed, user-defined workspaces that allow users to grant other users access to specific folders.
Users can share one or more folders in a Cell and manually assign permissions to one or more users. Users can also manage Cell’s internal visibility to decide whether other users are allowed to manage permissions.
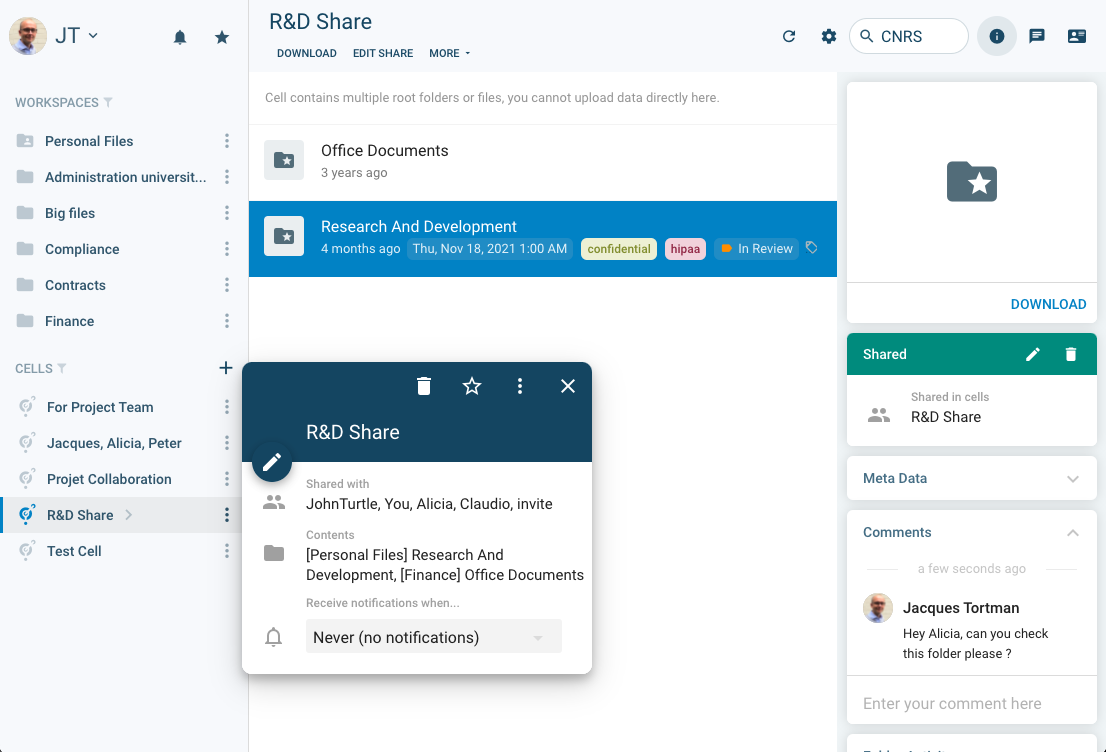
We say Cells are “sandboxed” because they inherit all the ACL defined at upper levels by admins: users can only share resources they have access to and can never provide more permissions than they have.
D - Advanced Reporting
On a day-to-day basis, ACL numbers can grow quickly as administrators assign roles and policies and users share resources with their co-workers. It can be quite hard to stay on top of “who is accessing what.” Authorization reports provide a quick way to display all permissions assigned to a tree by showing workspaces, cells and public links and their statistics (how many users have read/write access on this folder) at a glance.
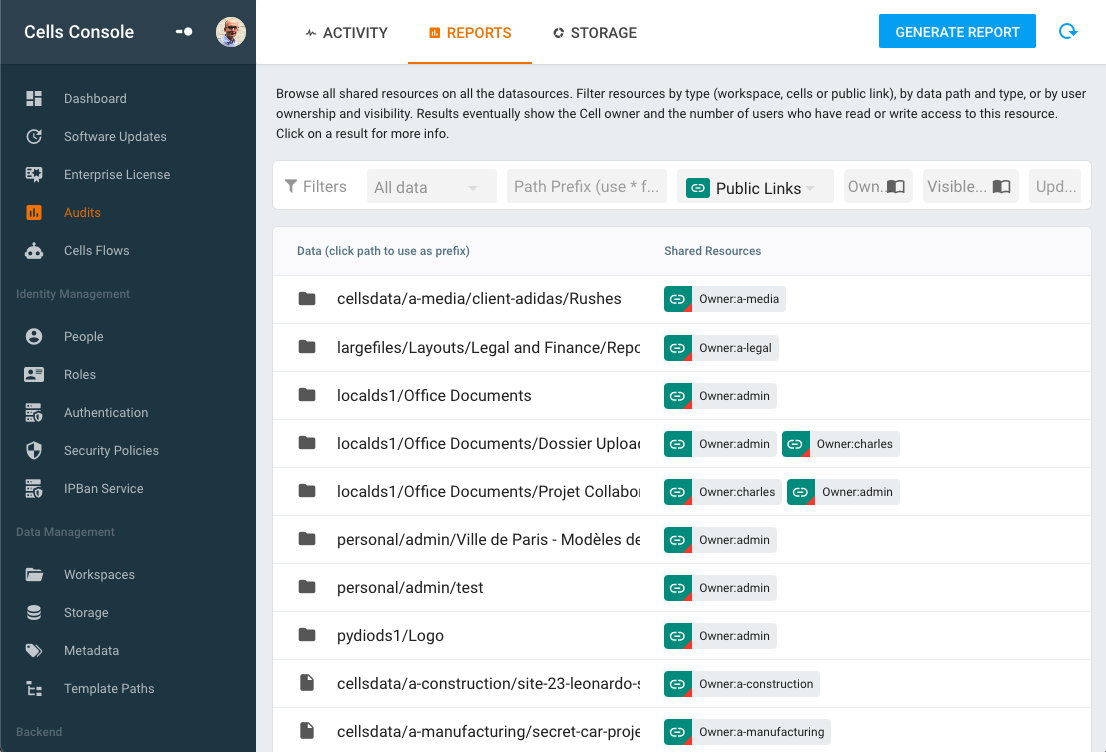
Typically, listing Public Links provides good visibility into files or folders opened “in the wild” by users with third-party partners. Links that aren’t password-protected or time-limited are flagged, allowing administrators to alert users that they probably should review their public links and eventually disable them.
E - Access Automation with Cells Flows
Assigning rights at a role level avoids having to manually assign permissions on a per-user basis. But some specific business processes may require automatically importing users from an external directory and creating specific workspaces or ACLs based on user-specific attributes.
Cells Flows workflow engine provides an easy drag-and-drop interface for programming automations that can perform these operations with custom filtering, automatic ACL assignation or workspace creation/deletion.
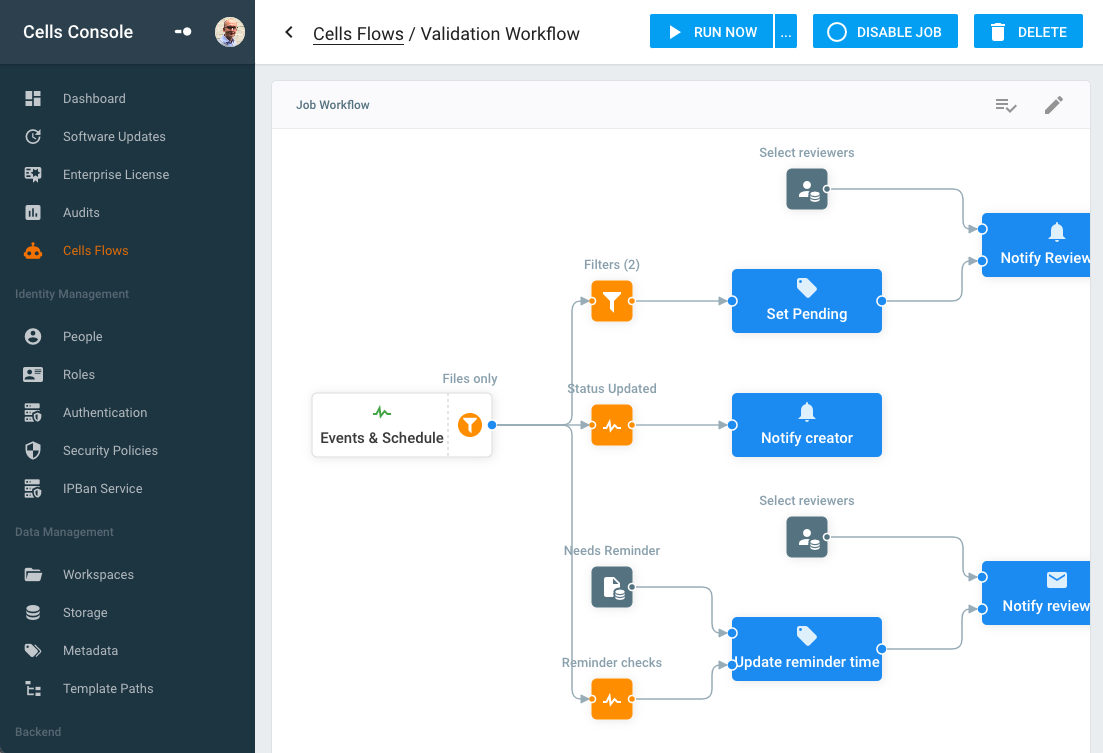
Automation increases productivity and reduces human error for both administrators and users, providing an extra level of control on all aspects of Cells’ identity management and access rights!
Need to Balance Ease-of-Use with Security? Pydio Cells Can Help.
If your organization is serious about secure document sharing and collaboration you need to check out Pydio Cells. Cells was developed specifically to help enterprises balance the need to collaborate effectively with the need to keep data secure.
With robust admin controls, advanced automation capabilities, and a seamless, intuitive end-user experience Pydio is the right choice for organizations looking to balance performance and security without compromising on either. Try Cells live for yourself. Or click on the button below to talk to a Pydio document sharing specialist.